Penetration Testing
The place for continuous Cyber monitoring
Keeping Safe ahead of the attackers
We want to keep you informed and explain how Cybersecurity penetration testing services can help your business.
The Australian Signals Directorate set out a document called the Australian Government Information Security Manual (March 2021) and recommends how businesses should apply Cybersecurity standards to stay ahead of Cyber gangs and crime.
Recommendations for Cybersecurity preparedness
- Have continuous monitoring plans
- Undertake an annual Cyber penetration test.
- Conducting vulnerability scans for systems at least monthly.
- Conducting vulnerability assessments or penetration tests for systems at least annually.
- Analysing identified security vulnerabilities to determine their potential impact and appropriate mitigations based on effectiveness, cost and existing security controls.
- Using a risk-based approach to prioritise the implementation of identified mitigations.

What is Penetration testing?
Did you know a Pen Test aim is to safely go as far and deep into the IT infrastructure to get to the electronic assets?
Pen Testing evaluates the weaknesses in a business’s IT infrastructure by discovering and safely exploiting gaps and weaknesses.
IT systems Weaknesses
We look for weaknesses in these areas of IT systems.
- Backoors in operating systems
- In software code
- Misconfigurations of software implementations
- Using software applications in a way it was not intended to be used
Network Endpoints
Pen Testing is conducted through manual or automatic tools, and these types of network endpoints.
- Devices that include Routers, Firewalls and Networks
- Servers
- Endpoint computers
- Wireless networks
- Wireless devices
- Software code and applications
The Penetration Testing Process
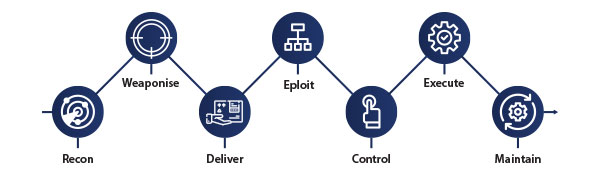
Penetration testing types to uncover weaknesses and vulnerabilities
Black Box testing
The minimum level of information or details is given to the tester about the Applications, Endpoints, or architecture being tested.
This is what happens in a real-world cyber-attack. The hacker does not know all the ins and outs of your IT infrastructure and will launch an all-out, brute force attack against the IT infrastructure, hoping to find a vulnerability or weakness that they can latch onto.
Grey Box testing
Grey Box testing where the attack surface is a defined scope of works
Since a tester has more knowledge of the client network, they will use manual and automated testing processes to focus their attention on Web Applications that will exploit possible weaknesses or vulnerabilities and possibly find more challenging security flaws.
Penetration testers will have partial knowledge of the Web Applications’ internal workings and face restrictions in getting access to all the software code and system’s architecture needed for testing.
Testing with a combination of the Black Box and the White Box tests will find more security holes, gaps and weaknesses, and this becomes the Grey box test.
White Box testing
This type of testing is a far more detailed testing type as the tester has full knowledge of software, it’s engineering and access to the Application’s software architecture and is looking for exploits and vulnerabilities in the source code.
However, more research time is needed when deciding on what to focus on regarding system and component testing. Analysis and sophisticated tools are required to conduct these tests, such as software code analysers and debuggers.

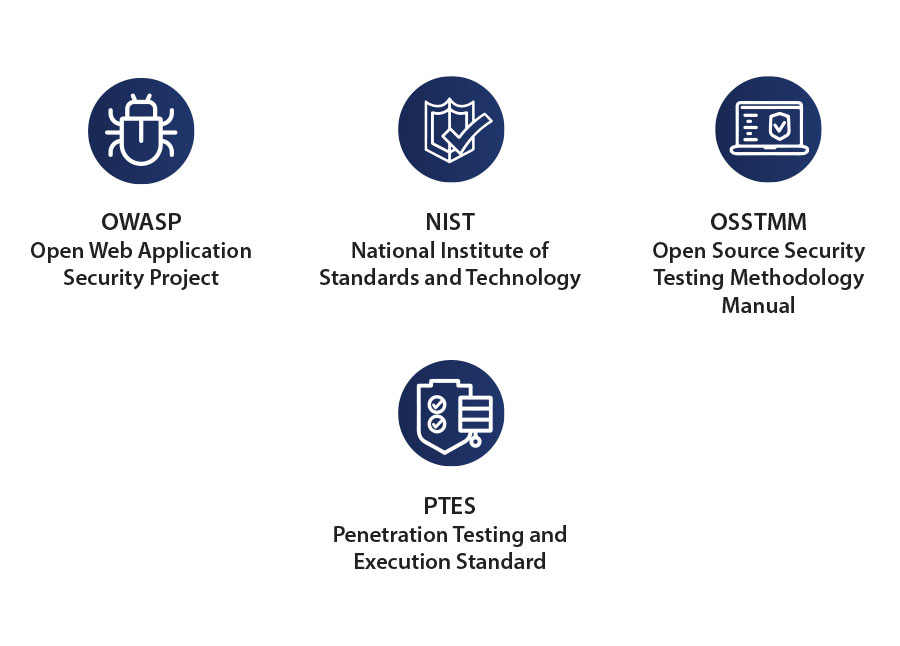
Penetration Testing Standards that we provide
- The Open Web Application Security Project (OWASP)
- The National Institute of Standards and Technology (NIST)
- Open Source Security Testing Methodology Manual (OSSTMM)
- Penetration Testing and Execution Standard (PTES)
Penetration testing types to uncover weaknesses and vulnerabilities
Ransomware as a service style attacks is proving extremely lucrative, with the most well-organised gangs earning millions per victim.
Cyber risks can affect your business and reputation. It does not matter what business you are in.
Essentially, businesses cannot function if systems are disrupted, shutdown or damaged—it is about being prepared for an attack.
Preventing Ransomware attacks is a huge task requiring the right services and tools to manage this.

Risk Assessments will look at stopping attacks before they happen.
This is where we consult with you to determine which vectors or entry points are the most concerning to you for validating a resilient IP Networking and Cyber operation practice at your business locations.
We would like to understand what your Cyber posture means to you, have you validated before, and a clear understanding of what posturing standard you seek?
Risk assessments are designed to be repeated repeatedly, dependent on your Cyber risk posturing needs that will reduce threat surfaces and the possibilities of an attack.
Threat Hunting Vectors for testing
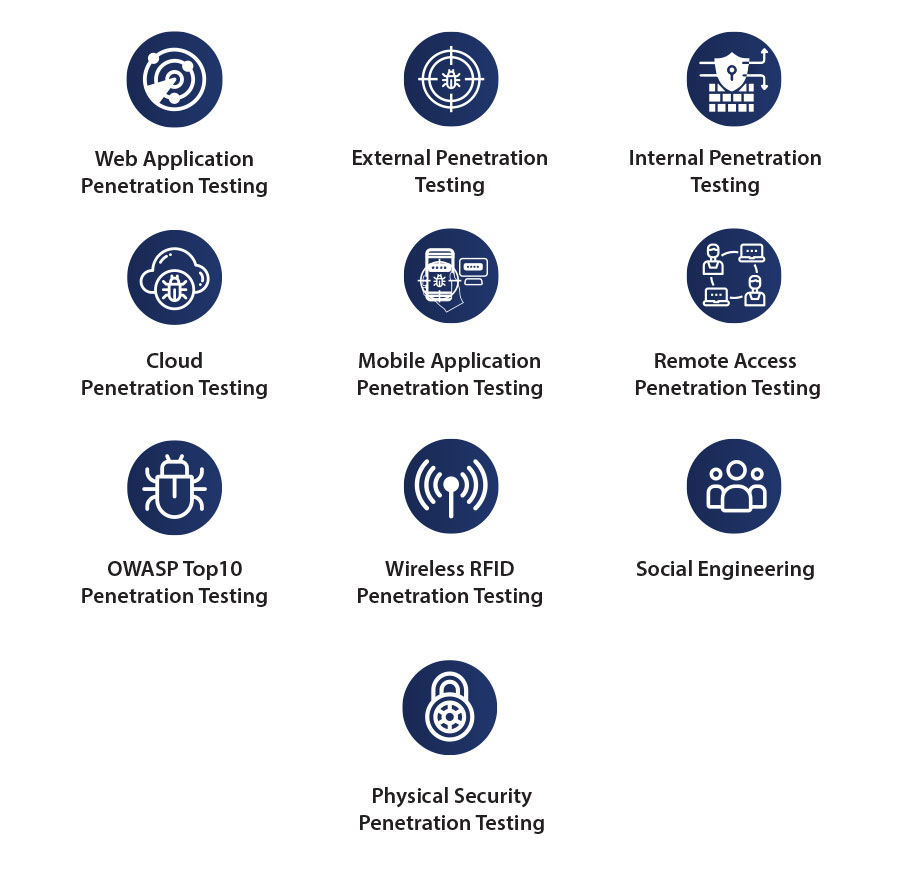
How Penetration tests are conducted
Our team of experienced and certified ethical hackers will help you identify and remediate vulnerabilities before criminals and hackers find them.
We offer a range of testing services, including but not limited to web application, infrastructure, wireless, mobile penetration testing. We can even add physical penetration testing to our cyber tests to provide end-to-end assurance against targeted attacks and corporate espionage.
Our engagement process is simple, and we are here in person and over the phone to assist at every stage.
How service is provided
- Consultations with key stakeholders.
- Decisions on testing per requirements needs.
- Developing your scope of works requirements for your Pen testing.

Prepare for Pen testing
- Communicating with your stakeholders and team members to expect malicious activities on your network
- If working in a live environment, make sure your back-ups are up to date
- Check your system’s permissions that you have access to all the systems that are undergoing testing is made available
- Start Pen testing
- Analysis and reports
- Advising our remediation steps
- Validation repeat of Pen testing procedure will ensure the validation steps achieved during your tests have met your posturing outcomes
- Implementing plans for red teaming, threat protection, and validation services will keep you always prepared for an attack.
Contact a Visionspeed representative to discuss how to harden your IT systems and prepare in the event of an attack.
