Ransomware Protection
The best way of staying safe against Ransomware attacks in Australia
Get the know-how and get a Cyber specialist whose actively tackling those mountains of worms. Seek your Cybersecurity preparedness and try Ransomware protection by Visionspeed
Our Sydney business is providers of Ransomware protection services against a ransomware attack.
It’s available here as a monthly service that aims to care for your Cybersecurity safety at all times proactively.
This page provides you with up-to-date information on “what is Ransomware” and how to protect against it.
We recommend that everyone starts with training about Cybersecurity essentials and gets the know-how of how to get their IT house’s into order before anything unfortunate happens.
It is significantly essential now to reduce those attack surfaces and not be a target for malicious hackers.
Please give extra attention to identity & permissions management, and give more time to privileged user accounts as these groups of users are the most significant targets of the hackers.
Try us out for your Cybersecurity with Visionspeed.com.
What is Ransomware?
Cybercriminals use ransomware to deny you access to your files or devices. They then demand you pay them to get back your access[1].
What you need to know about Ransomware?
- Apart from hackers, people are also likely to be a cause of data breaches. It is just as likely to be the person sitting next to you. Data breaches can result from human error
- Patch and patch and patch. These days now, servers are getting hacked as fast as you can count. When new threats emerge, you only have two days to patch your systems or face the hackers that are ready to attack[2]
- For customers, the impact of a data breach is almost always irreconcilable
- The security industry in 2021 reports that the average loss of downtime, productivity and recovery from a single attack can be around ten times the cost of the ransom[3]
- Data breaches can be detrimental to your business’s brand, meaning a loss of revenue and ultimately a loss of customer trust
- 60% of all businesses that are Ransomware attacked will cease trading within six months[4]
- Today’s Ransomware attacks do not discriminate businesses of all sizes and sectors are susceptible to attacks. However, small to medium businesses (SMB’s) are often less prepared to deal with[5]
- Small businesses are largely in the dark about the frequency and severity of ransomware attacks
- Extremely sophisticated computer worms now exploit multiple previously unknown vulnerabilities that will infect computers and spread. We now need a set of specialised services that will prepare and better protect us from Ransomware cybercrime
- Stopping Ransomware is a human problem, and you need a team to stop this and keep the hackers out of our networks. Lesson one is don’t get phished
- Most data breaches occur within businesses with 100 computer users or less
Ransom fees are prescribed and based on your net worth and ability to pay these fees[6] - The best practice is to regularly have cyber check-ups that understand gaps and weaknesses in your endpoints. Validation and remediation steps are your answer to fighting hackers and your unseen adversaries
- Criminals now download and retain large amounts of data from the company, threatening to release it publicly if the company does not pay up. Contact and identity information is the most common type of stolen information in a data breach
- Each time a person or business pays a ransom fee, cyber criminals use these fees to continue their cyber threat campaigns and next Ransomware attack victims
- Its purpose is to infect P.C.s and collect a ransom fee. However, they may accidentally cause real-world effects as cyberattacks on physical infrastructure and facilities can bring colossal safety and economic dilemmas for all those affected.
How does Ransomware work?
Attackers infiltrate your devices and spread throughout your networks, and encrypt your data, making it completely unusable and holding you to a ransom payment by Bitcoin before any attempt to restore it.
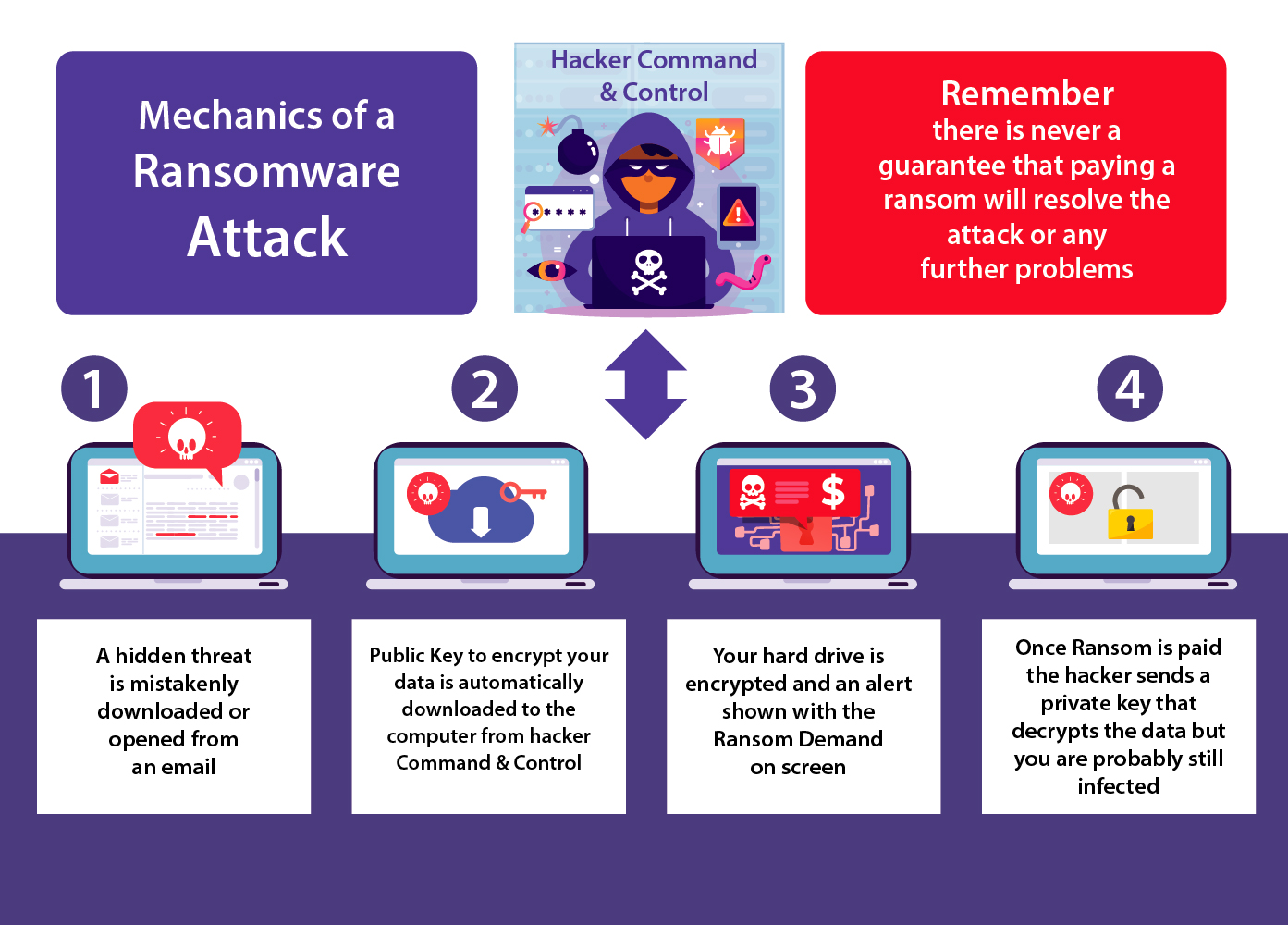
Ransomware attack steps
- From simple emails received in your inbox, a hidden threat is mistakenly downloaded and opened; they can take over the victim’s computer.
- In the second stage of the attack, the hacker’s server is contacted at their command and control where a public key is automatically downloaded to a compromised computer.
- The next stage is encryption of hard drives that then spread to all other drives and computers. A note is brought to your attention with ransom demands details to decrypt your data.
- Finally, once ransom is paid, the hacker sends a private key that decrypts the data they attacked*
*We recommended not paying the ransom fee. You are financing the hacker’s ability to continue hacking other targets or even yourself again.
Why is Ransomware your biggest threat?
The Internet is too often considered safe for sharing information, transacting information, and delivering products & services.
Ransomware threats are growing more severe as the developers of these platforms now rent out Ransomware as a service (RaaS) platform on the dark web to any would-be attackers. With the addition of “RaaS” platforms, there is now a greater significant threat than ever.
The owners of these platforms request a percentage of the profits as a commission back to its developers, and attacks are now most certainly gain in momentum.
The Office of the Australian Information Commissioner (OAIC) received 539 data breach notifications (up 5%) during the last period 1 July to 31 December 2020. Data breaches resulting from human error accounted for 38% of notifications, up 18% from 173 notifications to 204[7].
For today’s companies, falling victim to one of these attacks is no longer a question of “if” but “when”? People don’t think it will happen to them.
With the adoption of the multi-cloud, attack vectors and threat surfaces are growing exponentially. With IoT in a more connected world, we may only be 1 step away from an attack. Look at your business ecosystem and suppliers. Are they safe from Cyberattack?
Unlike machines that are programmed to carry out tasks, humans are fallible and can make mistakes that result in data breaches.
More work is required around Cybersecurity awareness to be being better prepared for a Cyber-attack. The problem is more significant and growing. Ransomware attacks now represent 15% of all Cyber incidents in Australia[8].
These days, communicating cybersecurity is confronted with paradoxes, which has resulted in society not taking appropriate measures to deal with the threats.
What happens to you if one of your suppliers is affected directly or indirectly by a Ransomware attack? Many Australians think it will not happen to them or believe someone else from I.T. is looking after me.
Read more in “Best tips to mitigate high risk Ransomware attacks”. We show how to start protecting yourself, think before you click, awareness training to end users and avoid data breaches. As humans we are often the weakest link in the cybersecurity chain. It pays to focus on strengthening your organisation’s security posture and awareness-training for staff.
People might say they have insurance against Ransomware, but did you know insurance premiums are likely to increase due to the increases in Ransomware activities. Future ways to keep your premiums in check is to have a good security validation result for your business.
All companies need to plan for the worst, with mandatory cybersecurity training for all employees and the recommended solutions for mitigating the risks.
Businesses need to look at their technology to ensure solutions in place that can offer both backup and protection if a data breach occurs.
Read more from our blog space
https://visionspeed.com/fighting-the-cyber-threat-in-your-business/
Who are the most significant Ransomware targets in Australia?
According to the O.A.I.C., human error, malicious or criminal attacks, and system faults are the top three reasons why data breaches occur within Australian companies.
The most prominent Ransomware targets are small businesses with 100 users and less[9] because they are less resourced to operate the Cybersecurity protection requirements needed than in larger business counterparts. They find it hard to understand the risks and combat against the ever-growing vectors and threat surfaces that arise with acceleration and adoption to the multi-cloud net-space.
Small companies have the most significant level of risk to Cyberattack as having less budget to Mitigate Cyber threats, carry out data hygiene activities and staff training, all with next to no resources available to deal with these pressing issues.
Latest Ransomware scorecard
The extent and severity of these attacks stopped these companies from normal operations and disrupted the public, associated businesses and creating public health concerns.
The top Five industries affected by Cyberattack are Health as the highest reporting industry sector, followed by finance, education, insurance, legal, accounting and management services [10]
High profile casualties of Ransomware
- Toll Australia – Ransomware attacked twice in a single year[11] 2020
- Spotless Group Ransomware[12] 2020
- Nine Entertainment Ransomware[13] 2021
- Colonial Pipeline[14] Around the world, we have seen another ransomware attack with a significant US fuel pipeline shut down, underscoring critical infrastructure vulnerabilities, and protecting operational technology (O.T.) and being ready for Cyberattack is vital 2021
- Acer computers in Taiwan faced a Ransom attack and fees of 100 Million dollars as hackers breach the network[15].
Ask yourself, can you live without your data? Can you afford adversaries, competitors, or enemy states to steal your intellectual property and data?
Please, do not become Australia’s next Cybersecurity statistic. Call the Visionspeed Cyberteam for an evaluation that starts a sound managed Cyber protection strategy for your business.
Best tips that mitigate high-risk Ransomware attacks
Cybersecurity according to the OAIC, SMBs are the prime targets of cyber-attacks.
Our aim is to enable businesses to undertake risk assessments and take appropriate actions that secure your data networks and user environments using this framework.
- Implement trainingprocesses that can identify phishing threats amongst your external emails. The best way to prepare employees in stopping Ransomware attacks is to train them. Train new employees at orientation and all employees bi-annually with simulations, validations and remediation activities that refine and check your Cybersecurity postures more regularly than before
- Have safe browsing habits.Ensure that employees understand all risks that access sites safely using the HTTPS secure communication protocol. Also, show employees how to check URL links that will reveal the complete URL at the bottom of the browser when hovering the mouse over a link
- Control user access to computers. Protect the highest privileged user accounts by creating low-level access account for their everyday use
- Password management and introduce multi factor authentication (M.F.A.).
It is widely known that people often use a document that contains all their passwords in one easy to reach the accessible file. This is genuinely unsafe, and you need standards in place that enforce the correct use of password stores and be applied by all. Implement robust password policies that expire every 90- days or less
- Understand “How to spot socially engineered Cyber Scams”. Teach employees about phishing, baiting, quid pro quo, pretexting, tailgating, Inbox Scams, Red Flags and Pop-Up scams. Explaining how these scams culminate and knowing how to spot them is a great way to reduce your attack surface
- Deploy firewalls, VPN and antivirus. Firewalls monitor incoming and outgoing traffic based on a set of configurable rules. Firewall technologies ensure that your network and endpoints are not vulnerable to attacks by separating your secure internal network from the Internet
Firewall appliances offer other abilities, such as backup connectivity with wired and wireless 4G/5G options, along with virtual private network delivery (VPN) that secures your remote workers
- Patch operating systems, applications, and antivirus services by having a patch management plan in place. This will ensure the Cyber criminals cannot exploit software vulnerabilities using a wide range of strategies that gain access to your computers. Be highly vigilant about patch management
- Configure Microsoft Office macro settings to block macros from the internet, and only allow vetted macros either in ‘trusted locations’ with limited write access or digitally signed with a trusted certificate[16]
- Scan emails and attachments to detect and block malware. Modern antivirus services can protect against Ransomware, keyloggers, rootkits, trojan horses, worms, adware, and spyware
- Data backup. Daily back-ups are a requirement to recover from data corruption or loss resulting from security breaches. Consider using a modern data protection service that takes incremental backups of data periodically throughout the day to prevent data loss
- Encrypt your data and make it inaccessible to anyone else
- Maintain offline, encrypted backups of your data and regularly test these backups. Keep back-ups offline or in a separated network
- Request advanced solutions from your trusted Cybersecurity provider for protection against malicious URL’s, phishing attacks, social engineering techniques, identity theft, permissions management, and denial of service attacks
- Data loss prevention services that set deception traps. Be looking for hackers trying to hide inside your networks. Deception traps take the form of honey pots and breadcrumbs that provide the earliest warning signs, intent and understanding of the skill level of hackers and especially what they are attempting to steal
- Conduct a security risk assessment. Validate your Cybersecurity with Penetration testing. This helps to shape a security strategy that meets your specific needs. Outcomes provide a report of gaps and weaknesses found within your network. Remediate threats in order of priority and your I.T budget
- Know where your data resides Maintaining a view of where your business data is located is an important step to keeping ahead of your adversaries. The more places that data exists, the more likely it can be accessed by unauthorized individuals
- Use key card measures and look at C.C.T.V surveillance.
Visionspeed Cyber
Visionspeed Cybersecurity provides readymade Cyber solutions that protect your business against Ransomware threats, phishing protection, intrusion prevention and training for your staff.
We provide a highly effective Ransomware protection service covering endpoints and O.T. environments from the ground to the cloud and complimented with add-on Layer 1 technical solutions available nationally.
All it takes is one click by an employee to put your data in jeopardy. Protect your business with Ransomware protection solutions with a local expert you know and trust.
Validate, remediate, and reduce your threat surfaces with Visionspeed Cyber.
